The number of cyberattacks is rising, and so is their complexity. Therefore, most segments of the healthcare value chain are vulnerable to attack. The figure below details the areas of cybersecurity in which medical device companies should focus their time and resources. Medical device companies should invest in technologies that shaded green, explore the prospect of investing in technologies that are shaded amber, and ignore technologies that are shaded red.
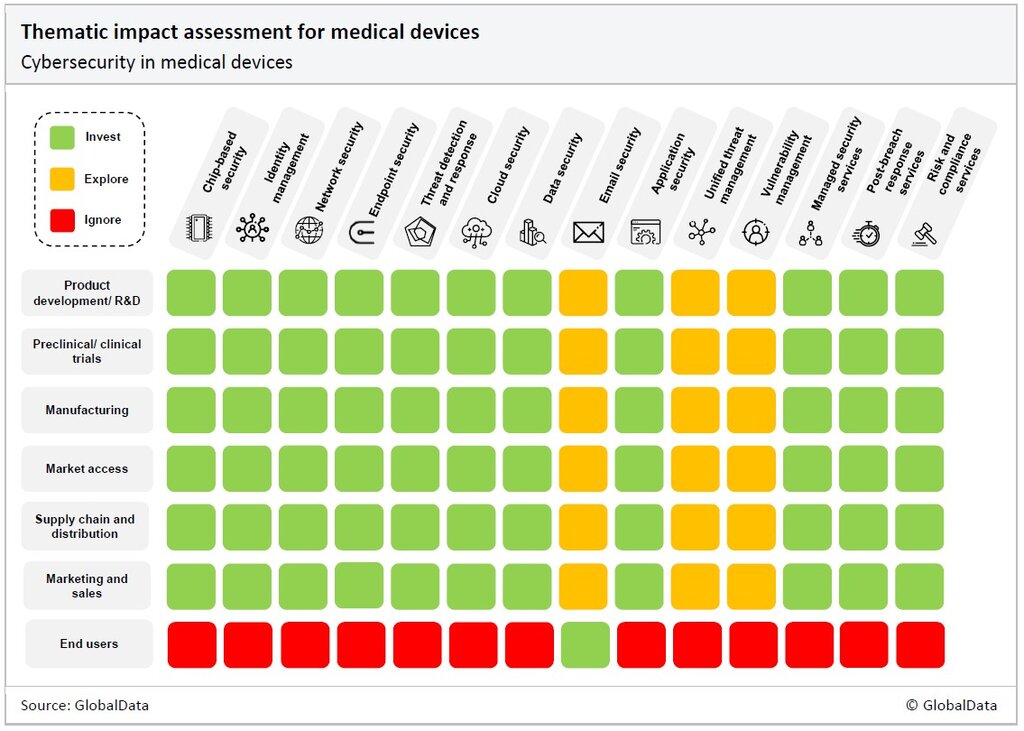
One blind spot in a company’s defenses is one too many, especially given that attackers seek vulnerabilities rather than indiscriminately attacking all potential weak points. All value chain components—from chips, identity procedures, networks, endpoints, cloud presence, data, email, and applications—must be covered.
Appropriate vulnerability management, threat detection, and threat response must be established. Outsourcing these measures to unified threat management, managed security services, and post-breach response services may be more viable than developing inhouse expertise and is worth exploring.
How does artificial intelligence impact cybersecurity?
AI enables more sophisticated cyberattacks and could accelerate the pace of innovation in malware. Hacking groups will likely use large language models (LLMs) trained on malware to target their attacks more effectively. AI techniques could help hackers bypass facial security, spam filters, and anomaly detection engines, and adapt to their environment to evade threat detection, among other things.
However, AI may enable more sophistication in cybersecurity defenses. Proactive defense systems powered by ML are being developed. However, since AI is specialized, healthcare companies will likely have to partner with AI start-ups or Big Tech companies to develop capabilities at pace and give those partners sensitive information. This poses operational security and regulatory risks.
How does big data impact cybersecurity?
The healthcare and pharmaceutical industries are key targets of malicious cyber threat actors due to the vast amount of valuable and sensitive data and IP they hold. Therefore, it is vital for life sciences companies to protect these assets. As the industry becomes more digitalized, cybercriminals have more avenues to steal personal and proprietary data, including from medical health records and connected medical devices.
Connected devices that collect personal health data, such as wearables, frequently exchange data with paired devices via Bluetooth, which makes them especially susceptible to hacking. Furthermore, individual devices that contain personal health information generally have little cyber protection and are often not connected to managed networks. Individual devices would benefit from implementing cybersecurity software like network security, vulnerability management, and identity management.
How does the effect of COVID-19 on digital innovation impact cybersecurity?
The rush to shift from office-based work to remote working and from in-person care to virtual care caused by the COVID-19 pandemic significantly increased cyber risk. The increased use of technology—especially cloud technology and connected devices—increased the potential attack surface, and the high speed of the transition meant many IT security teams had insufficient time to install adequate security defenses. Companies moved more sensitive operations and information online than ever before, making attacks more costly.
Soon after the lockdowns began, law enforcement agencies warned that malicious actors were piggybacking on the vulnerabilities created by the pandemic to further their attacks. Examples included phishing emails relating to the sales of fake test kits and personal protective equipment. In one case, android spyware was used to mimic the Johns Hopkins COVID-19 case dashboard, which provided data on COVID-19 infections and death rates. Attackers further targeted remote working tools, using fake requests to reset virtual private network (VPN) accounts, fake sign-in pages for video conferencing accounts, or bogus incoming chat requests from colleagues on corporate messaging systems.
The proportion of attacks targeting home workers increased from 12% of malicious email traffic before the UK’s lockdown began in March 2020 to more than 60% six weeks later, according to cybersecurity company Darktrace.
The stress and urgency placed on hospitals weakened their resilience to attacks, making them more attractive targets for attackers. Critical Insight reported that cyberattacks on healthcare companies increased by 35% in H1 2021. One attack early in lockdown forced Brno University Hospital, one of the Czech Republic’s leading testing centers, to postpone surgeries and tests.
Companies involved in developing COVID-19 vaccines and therapeutics, including pharma companies, contract research organizations (CROs), and research institutes, became targets of cybercriminals looking to steal proprietary information about these products. Pfizer’s vaccine submission was stolen in December 2020 in an attack on the European Medicines Agency. Novavax and Johnson & Johnson reported that hackers had attempted to steal vaccine information.
How do connected devices impact cybersecurity?
A larger and more complex digital footprint is at greater cyber risk. Each connected device in a network represents a new node for an attack. Previously, when operational technology (OT) and IT networks were separate, the security risk was lower. Many healthcare companies have now integrated these networks. Such integration enables better data exchange, which is good for business. However, it also increases the potential harm from attacks, as a vulnerability in one network allows attackers into both.
Additionally, sensitive data is increasingly present on the network. The ongoing trend is shifting away from devices worn at discrete periods throughout the day, such as blood pressure cuffs or heart rate monitors, and toward those that continuously monitor health in a less invasive, seamless manner. This means that far more data is recorded and communicated. Thus, there is a richer bounty for successful attacks.
In October 2017, the FBI issued an alert detailing the possibility of cybercriminals targeting IoT devices (such as insulin pumps and pacemakers). Due to the limited computing power, IoT devices often have little or no internal security. Furthermore, measures that do exist are often unconfigured—famously, usernames and passwords are left as “admin” or other simple words, which attackers can easily guess. Successful cyberattacks against connected IoT devices jeopardize patient safety (such as with implanted insulin pumps or pacemakers). GlobalData estimates that 68% of medical devices will connect to provider networks by 2025.
How do digital therapeutics impact cybersecurity?
Cybersecurity is a concern for DTx, whether the products are in clinical research evaluation or ready for market release. As DTx move information through the internet, the risk of cyberattacks is high and could jeopardize both trust in the product and the care of the patients in question. Examples of dangers to DTx include data theft, loss of data, and violation of data protection.
While DTx differs from medical devices (where, for example, cyberattacks could disrupt critical medical functions), cybersecurity needs to mirror the regulations imposed on the medical devices industry. DTx could even be more vulnerable to cyberattacks than medical devices, as they often depend on third-party software, including operating systems like iOS and communication networks. These follow safety standards that could be less meticulous than the standards for medical device.
If a wellness app wants to establish DTx, determining the cybersecurity risks becomes more important as DTx uses protected health data while wellness apps do not. The wellness apps wanting to establish DTx will need to answer vital cybersecurity questions if these apps switch to DTx, as regulating bodies like the FDA will perform a rigorous cybersecurity evaluation. Establishing cybersecurity risks and vulnerabilities will be key in preparing DTx products for large-scale adoption.
How does cyber hygiene impact cybersecurity?
A large proportion of successful cyberattacks penetrate old systems using outdated cybersecurity measures. As these measures were built when cybercrime was a lesser concern, they have insufficient defenses and are vulnerable to modern attacks. They often involve passwords embedded in the software code or easily breached data networks.
In the case of operating systems for which development support has been discontinued, vulnerabilities will not be patched even when they are known. Any threat actor who knows that an operator uses such an operating system also knows which vulnerabilities to try first. The NotPetya attack on Merck & Co, the costliest cyberattack the pharma industry has seen so far, worked on Microsoft systems that had not installed a necessary security patch. Outdated systems no longer have patches developed, so even if their installation is desired, it is impossible.
Often, where too many devices using too many different systems are used together, such as security management for hospitals, there is a requirement for more resources than are available. Comprehensive, centralized security approaches are infeasible beyond a certain point. Effective network segmentation prevents malware and viruses from spreading across the entire organization's networks by limiting access to medical data. It can also act as a good and cheap antidote to the prevalence of legacy systems, as vulnerable devices can be kept in separate networks from sensitive information.
A lack of effective network segmentation was responsible for the damage caused by several cyberattacks, including the 2017 WannaCry global ransomware attack that targeted computers running Microsoft’s Windows operating system. Furthermore, many devices have data sharing and management functions active and open to other devices on the network by default, such that malware from one device can be easily transferred onto other devices, creating the potential for a breach to cascade throughout multiple systems.
Sophisticated authentication tools reduce cyber risk significantly. Modern tools include multi-factor authentication and biometrics such as fingerprints and facial recognition. For example, the Community Hospital Anderson of Indiana implemented biometric authentication in 2017. Multi-factor authentication has also become a requirement in the UK’s National Health Service (NHS) in 2024. However, healthcare still broadly uses passwords, which are unsophisticated and easy to hack, especially when employees are careless with them.
How does regulation impact cybersecurity?
As the healthcare industry has shifted towards EHRs and telemedicine, companies now hold and process much more sensitive patient data and, consequently, are more likely to fall afoul of patient data regulations. Additionally, the regulatory environment is becoming stricter.
Regulations such as the US’s Health Insurance Portability and Accountability Act (HIPAA) and the EU’s GDPR reflect and enforce an emerging intolerance for the mishandling of sensitive data. The liabilities and penalties associated with data breaches are far more severe than they were previously.
The consequences of failing to comply with regulations can be quite severe. In 2022, a psychotherapy center was fined $639,800 under GDPR because its patient data server had no firewall. Also in 2022, a Danish COVID-19 test center shared data on a WhatsApp group that contained all of its employees and was fined $84,900. Furthermore, a Hungarian public authority was fined $29,100 for keeping COVID-19 test data and patient and doctor contact information in a single unencrypted Excel spreadsheet.
At the beginning of 2023, the Federal Trade Commission (FTC) fined GoodRx, an American telehealth platform, $1.5 million for sharing personal health data with Meta, Google, and other parties.
Apart from these rigorous data protection acts, several other regulations have been recently implemented to strengthen cybersecurity in the healthcare sector. For example, the ECCS, issued under the EU Cybersecurity Act, will require healthcare companies to comply with the EU’s certification process, where self-assessment is not allowed. Healthcare companies will have to disclose their cybersecurity vulnerabilities. This will help ensure that healthcare organizations adhere to stringent cybersecurity standards.
At the beginning of 2024, the Healthcare Cybersecurity Improvement Act of 2024 was introduced in the US. This bill aims to enhance cybersecurity in the healthcare sector. It will incentivize healthcare companies to meet the minimum cybersecurity standards to receive monetary help if they experience a cyberattack.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.