Cyberattacks are especially dangerous to healthcare. Weak cybersecurity measures expose companies to serious risk. Victim companies suffer operationally, as systems are rendered unusable; reputationally, as customers lose trust; and legally, as ever-stricter regulators seek to punish.
The healthcare industry is particularly vulnerable because it uses extremely sensitive data. Pharma companies have proprietary scientific data and intellectual property, medical devices companies develop connected devices, and healthcare companies collect and utilise patient data. Additionally, operational functions are often literally matters of life and death. Breaches in healthcare and pharma cost more than those in almost any other industry.
Here we look at the role and importance of cybersecurity within the healthcare sector and how healthcare companies are developing increasingly sophisticated measures to prevent cyberattacks.
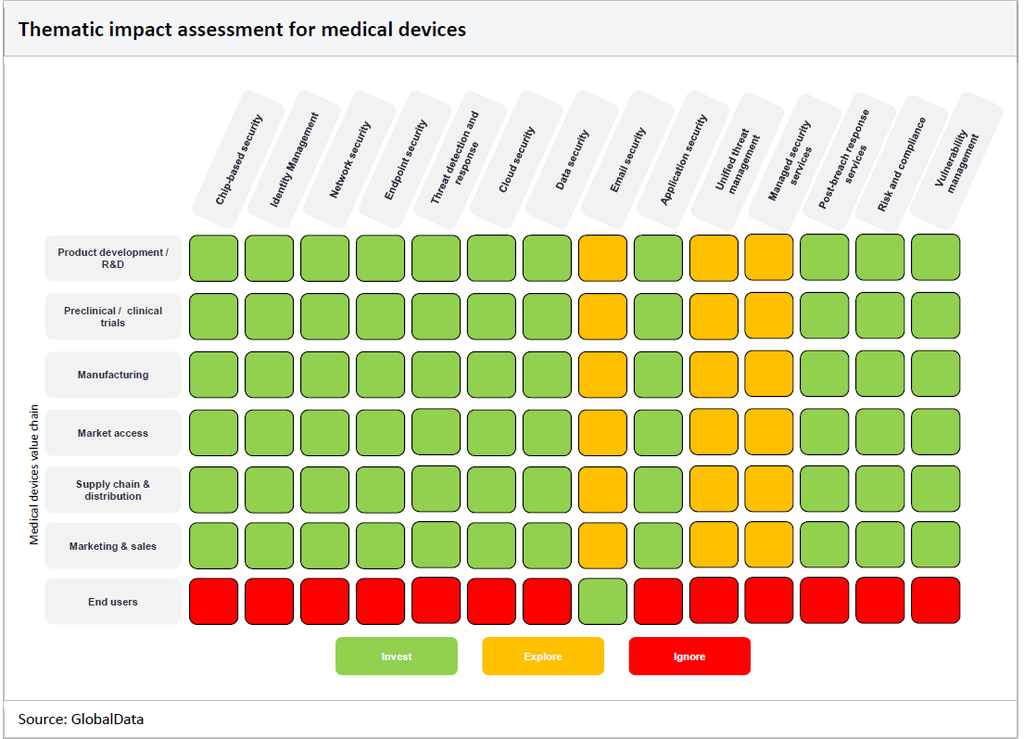
The matrix below details the areas in cybersecurity where medical device companies should be focusing their time and resources. We suggest that medical device companies invest in technologies that are shaded in green, explore the prospect of investing in technologies shaded in yellow, and ignore areas shaded in red.
How does Covid-19 impact cybersecurity?
The rush from office-based work to remote working and from in-person care to virtual care and digital monitoring caused by the Covid-19 pandemic significantly increased cyber risk. The increased use of technology—especially cloud technology as well as connected devices—increased potential attack surface, and the high speed of transition required meant many IT security teams had insufficient time to install adequate security defenses.
Companies moved more sensitive operations and information online than before, making attacks more costly. Soon after the lockdown, law enforcement agencies warned that malicious actors were piggybacking on the vulnerabilities created by the pandemic to further their attacks. Examples included phishing emails relating to sales of fake test kits and personal protective equipment, and Android spyware being delivered through a popular university Covid-19 case dashboard.
Attackers targeted remote working tools, using fake requests to reset VPN accounts, fake sign-in pages for video conferencing accounts, or bogus incoming chat requests from colleagues on corporate messaging systems. The proportion of attacks targeting home workers increased from 12% of malicious email traffic before the UK’s lockdown began in March to more than 60% six weeks later, according to cybersecurity company Darktrace (Darktrace, 2020).
The stress and urgency placed on hospitals weakened their resilience to attacks, making them more attractive targets for attackers. For instance, hospitals were more likely to pay the ransom on a ransomware attack. Critical Insight reported that cyberattacks on healthcare companies increased by 35% in H1 2021. One attack early in lockdown forced Bruno University Hospital, one of the Czech Republic’s leading testing centres, to postpone surgeries and tests.
Companies involved in developing Covid-19 vaccines and therapeutics, including pharma, contract research organisations, and research institute, became targets of cybercriminals looking to steal proprietary information about these products. Pfizer, Moderna, Johnson & Johnson, AstraZeneca and other companies involved in vaccine development found themselves becoming household names. Pfizer’s vaccine submission was stolen in December 2020 in an attack on the European Medicines Agency. Novavax and Johnson & Johnson both reported that hackers had attempted to steal information on their vaccines.
As in-person consultations became more difficult, patients and doctors increasingly relied on digital monitoring devices. TriMedx’s cybersecurity team saw the number of cyberattacks increase from an average of 19 each month to over 80 during the pandemic.
Climate change is a persistent and important issue globally. Many countries and companies are trying their best to implement policies that will combat the rapid warming of the earth, but some industries are doing better than others. The medical device industry has been slow to change its sustainability practices, largely due to the strict regulations it faces.
Alexandra Murdoch, Medical Analyst, Medical Devices, GlobalData
How does cyber hygiene impact cybersecurity?
A large proportion of successful cyberattacks penetrate old systems still using outdated cybersecurity measures. Built when cybercrime was a lesser concern, they have insufficient defences and are vulnerable to modern attacks; often they involve embedded passwords in the software code or easily breached data networks. In the case of operating systems for which development support has been discontinued, vulnerabilities will not be patched even when they are known.
Any threat actor who knows an operator uses such an operating system knows which vulnerabilities to try first. The NotPetya attack on Merck & Co, the costliest cyberattack the pharma industry has seen, worked on Microsoft systems that had not installed a necessary security patch. Legacy systems do not even have patches developed anymore, so installation, even if desired, is impossible.
Where too many devices using too many different systems are used together, security management for hospitals demands more resources, often more than what is available. Comprehensive, centralised security approaches are infeasible beyond a certain point. Forescout’s study found more than 30% of the healthcare organisations had medical devices from more than 100 vendors on their network, and over 40% had more than 20 different operating systems.
Effective network segmentation, by limiting access to medical data, prevents malware and viruses from spreading across the entire organisation's networks. It can also act as a good and cheap antidote to the prevalence of legacy systems; vulnerable devices can be kept in separate networks from sensitive information. A lack of effective network segmentation was responsible for the damage caused by several cyberattacks, including the 2017 WannaCry ransomware attack.
Further, many devices have, by default, data sharing and management functions active and open to other devices on the network, such that malware from one device can be easily transposed onto other devices, creating the serious potential for cascading a breach throughout multiple systems. For example, 85% of medical networks surveyed in Forescout’s study that ran on Windows OS had the Server Message Block (SMB) protocol switched on; the protocol, intended to allow shared access to files between nodes on a network, is known to allow threat actors to move laterally through the network once breached.
Sophisticated authentication tools reduce cyber risk significantly. Modern tools include multi-factor authentication and biometric tools such as fingerprints and facial recognition. For example, the Community Hospital Anderson of Indiana implemented biometric authentication in 2017. But healthcare still broadly uses passwords, which are unsophisticated and easy to hack, especially when employees are careless with them.
Companies without appropriate response strategies for cyberattacks are more vulnerable to damage. The costs the UK’s National Health Service (NHS) sustained in the WannaCry attack were far worse for a lack of response strategy.
How do connected devices impact cybersecurity?
Simply, a larger and more complex digital footprint is at greater cyber risk. Each connected device in a network represents a new node for an attack. Previously, when OT and IT networks were separate, the security risk was lower. Many healthcare companies have now integrated these networks. Such integration enables better data exchange, which is good for business, but increases the consequence of attacks, as a vulnerability in one allows attackers into both.
Additionally, sensitive data is increasingly present on the network. The ongoing trend away from devices worn at discrete periods throughout the day (such as blood pressure cuffs or heart rate monitors) and toward those that continuously monitor health in a less invasive, seamless manner means that far more data are recorded and communicated. There is a richer bounty for successful attacks.
In October 2017, the FBI issued an alert detailing the possibility of IoT devices (such as insulin pumps and pacemakers) being leveraged by cybercriminals. Due to the limited computing power, IoT devices often have little or no internal security themselves. Furthermore, measures that do exist are often unconfigured – famously, usernames and passwords are left as ‘admin’ or other simple words, which attackers can guess with a dictionary attack. Successful cyberattacks against connected IoT devices jeopardise patient safety (think of, for example, implanted insulin pumps or pacemakers), and it is estimated that 68% of medical devices will connect to provider networks by 2025.
How does regulation impact cybersecurity?
As the healthcare industry has shifted towards electronic health records and telemedicine (the latter especially during Covid), companies now hold and process much more sensitive patient data, and consequently are more likely to fall afoul of patient data regulations. Additionally, the regulatory environment is becoming stricter. Regulations such as the US’s Health Insurance Portability and Accountability Act (HIPAA) and the EU’s GDPR reflect and enforce an emerging intolerance for the mishandling of sensitive data.
The liabilities and penalties associated with data breaches are far more severe than they previously were. In 2022, a psychotherapy center was fined $639,800 under the GDPR; their patient data server had no firewall. Also, in 2022 a Danish Covid test center passed data on a WhatsApp group that contained all the employees and was fined $84,900. A Hungarian public authority was fined $29,100 for keeping Covid test data and patient and doctor contact information in a single unencrypted Excel spreadsheet.
How does AI impact cybersecurity?
AI enables more sophisticated cyberattacks. Conceivably, AI techniques could help hackers bypass facial security, spam filters, and anomaly detection engines, and adapt to their environment to evade threat detection, among other things. Additionally, AI could accelerate the pace of innovation in malware.
It is true AI may enable more sophistication in cybersecurity defenses. Proactive defenses powered by machine learning are, though not widely adopted, in development. However, since AI is so specialised, companies will likely have to partner with AI startups or big tech companies to develop capabilities and give those partners sensitive patient information. This poses an operational security risk as well as a data privacy regulatory risk.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.